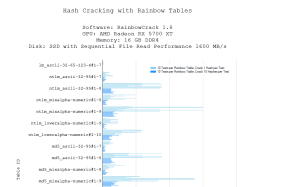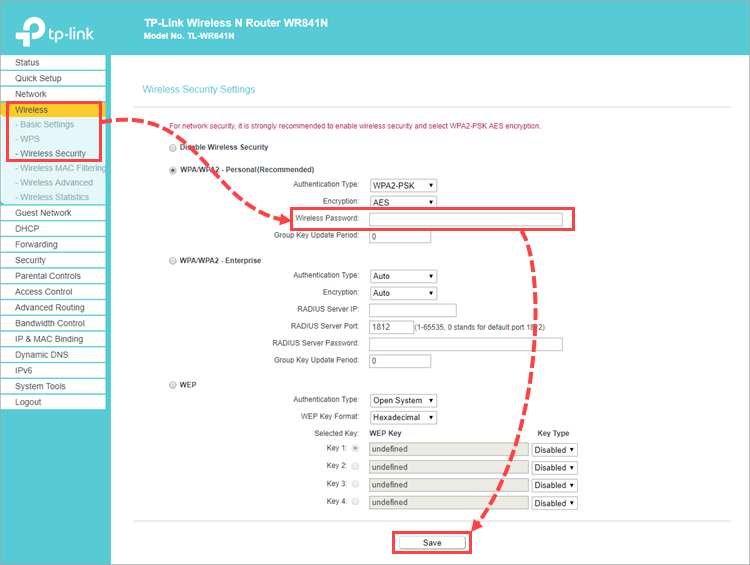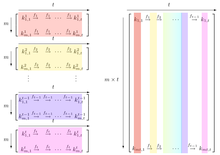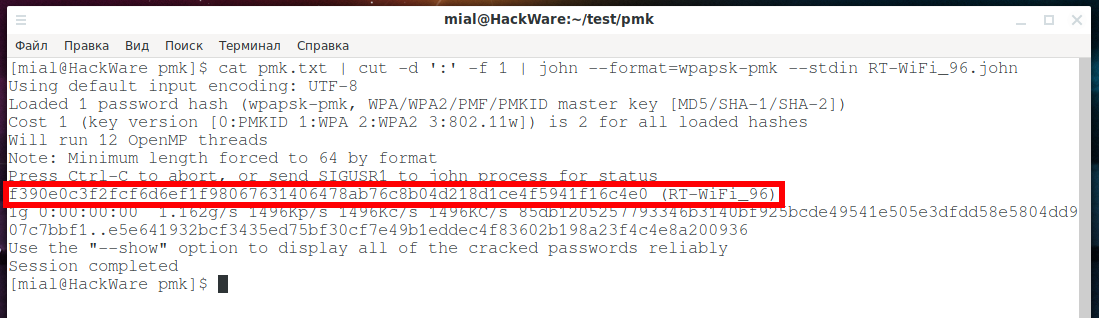
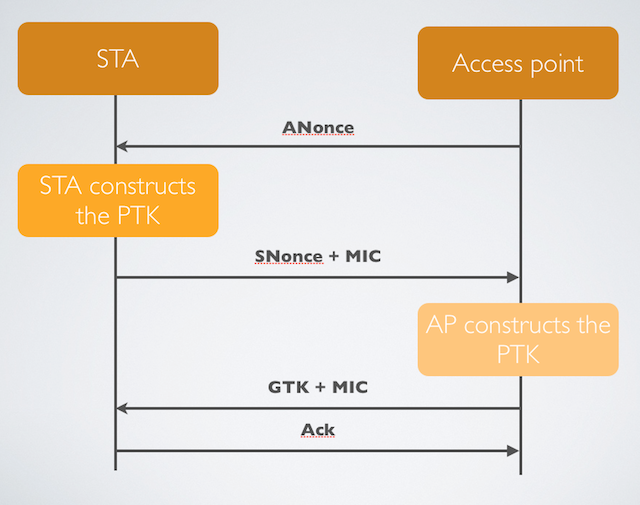
How to use precomputed tables to crack Wi-Fi passwords in Hashcat and John the Ripper - Ethical hacking and penetration testing
GitHub - Kidd3n/WifiPwnedd: Tool for Wifi Network Attacks (WPA/WPA2 - PSK- Hijacking - Rainbow Tables - Beacon Flood - DoS Attack - Scanner - Fake/Rogue AP - Force Brute with GPU).
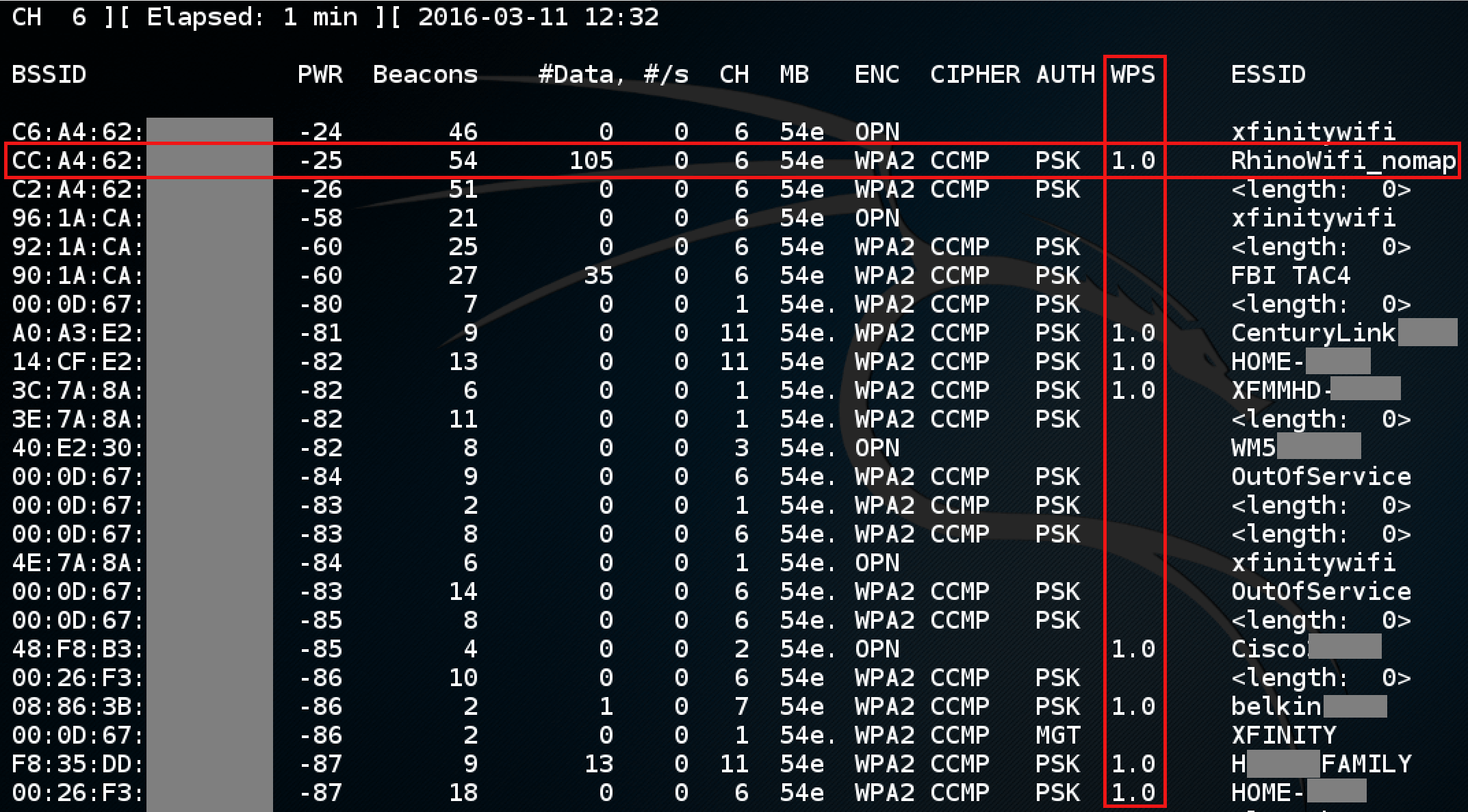
Cracking WPA/WPA2 Using Rainbow Table - Hacking WEP/WPA/WPA2 Wi-Fi Networks Using Kali Linux [Video]

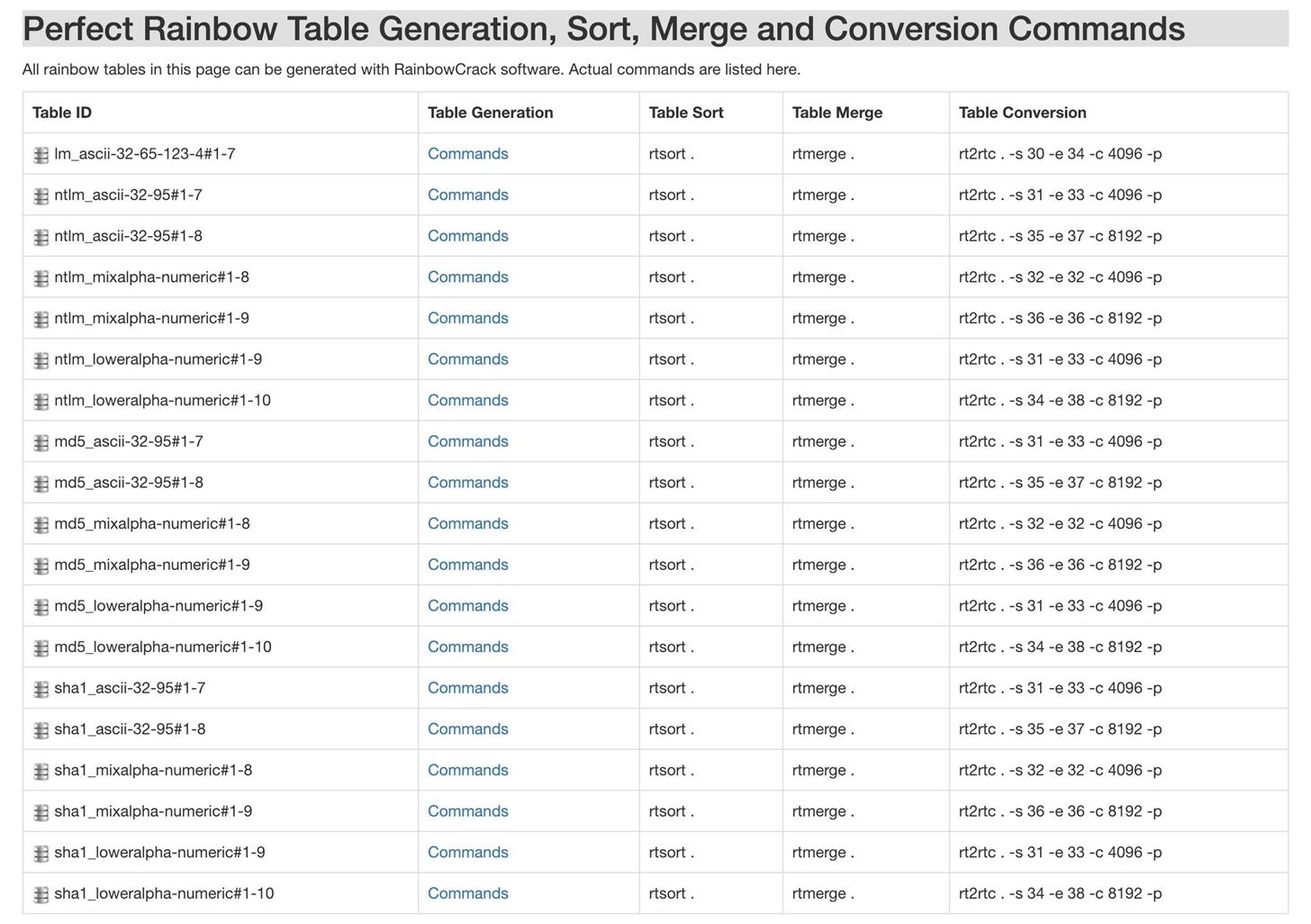
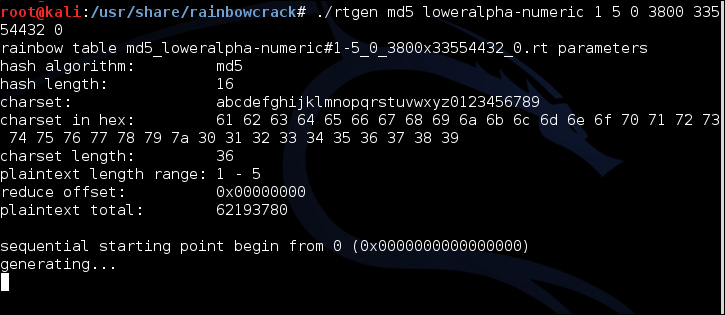
How to Create Rainbow Tables for Hashing Algorithms Like MD5, SHA1 & NTLM « Null Byte :: WonderHowTo
:quality(80)/images.vogel.de/vogelonline/bdb/345900/345976/original.jpg)

![Hashcat tutorial for beginners [updated 2021] | Infosec Resources Hashcat tutorial for beginners [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2018/04/122120-1.jpg)