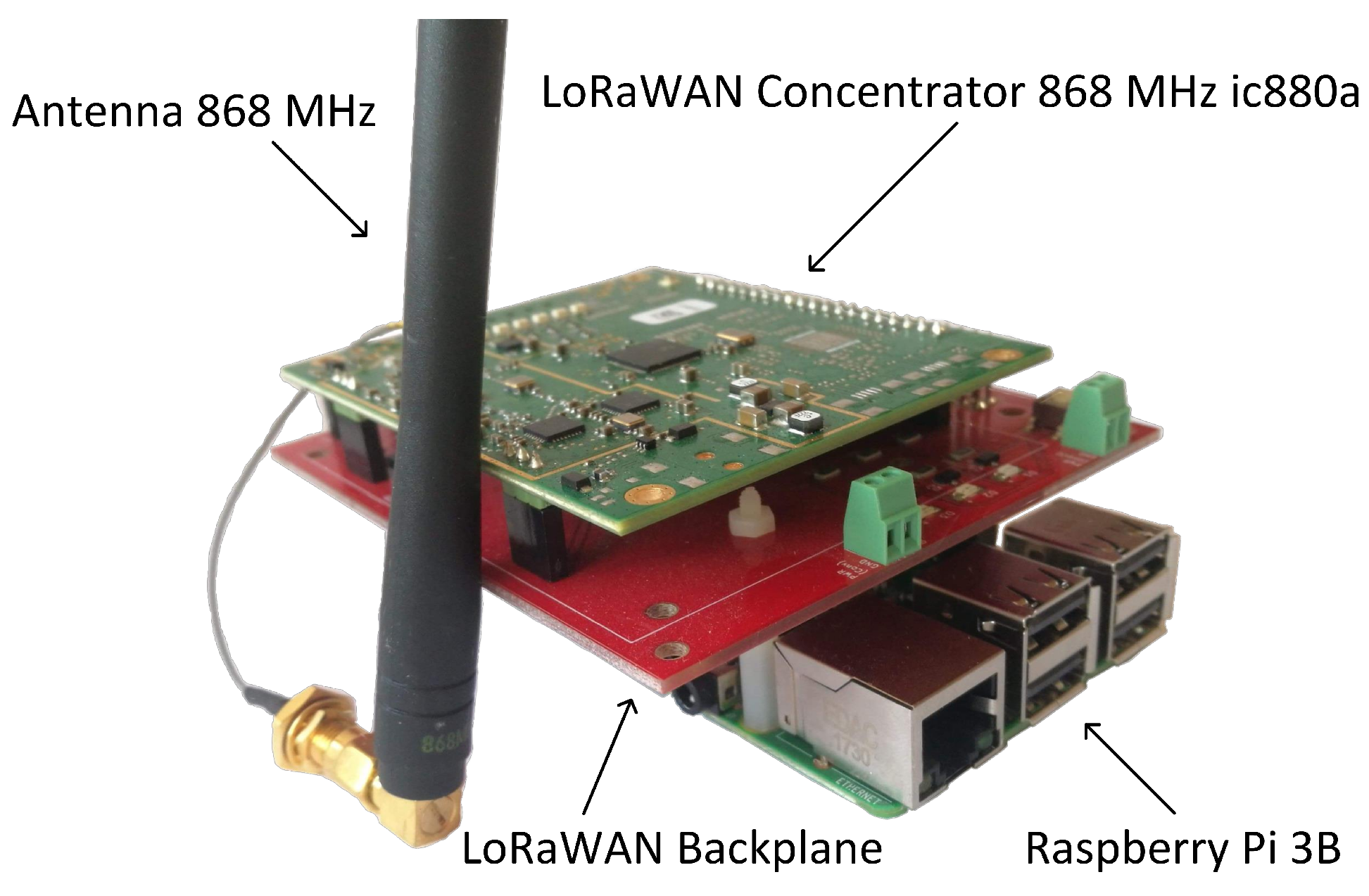
Applied Sciences | Free Full-Text | Testbed for LoRaWAN Security: Design and Validation through Man-in-the-Middle Attacks Study

How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo

How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo

How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo
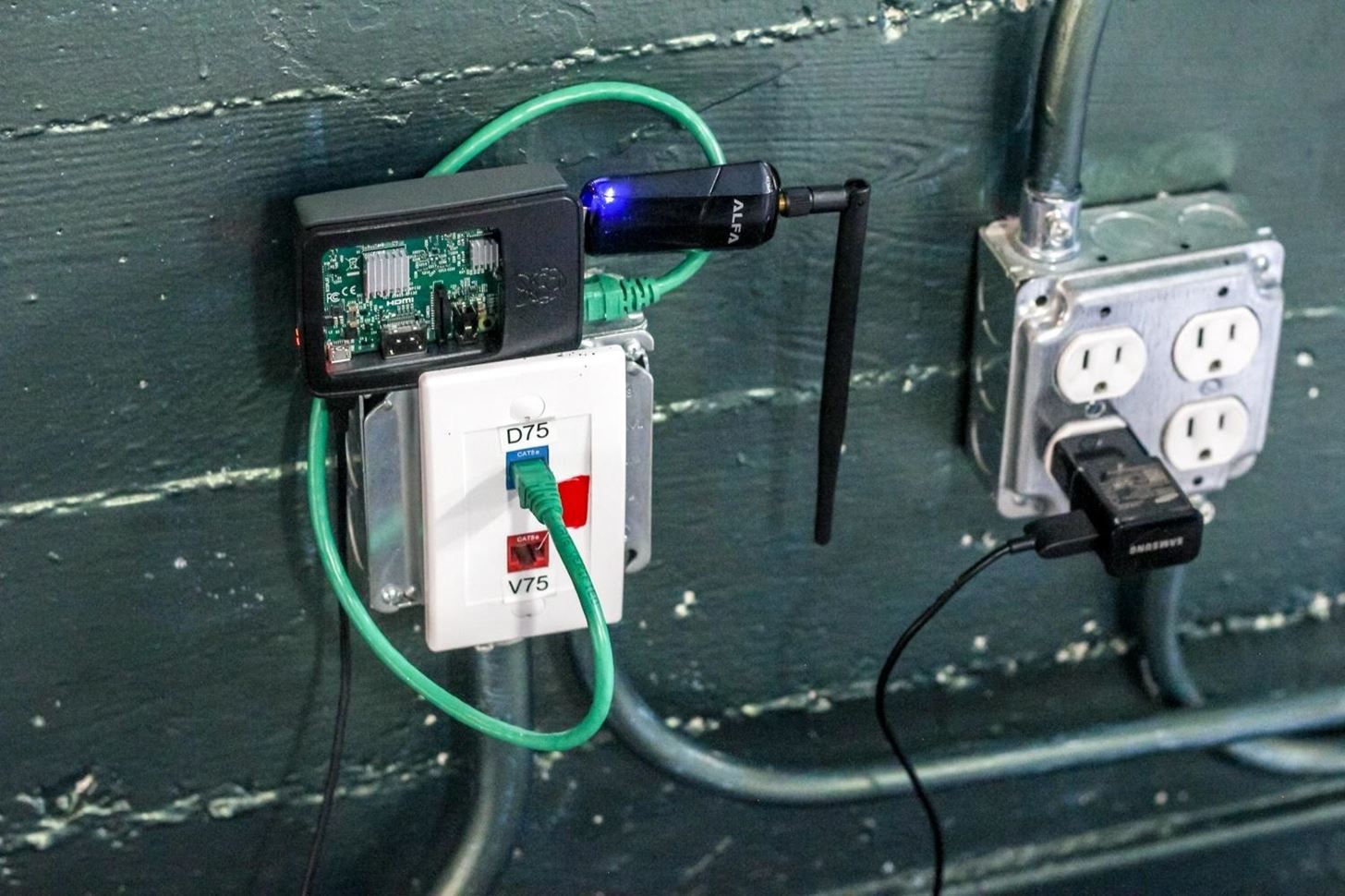
How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo

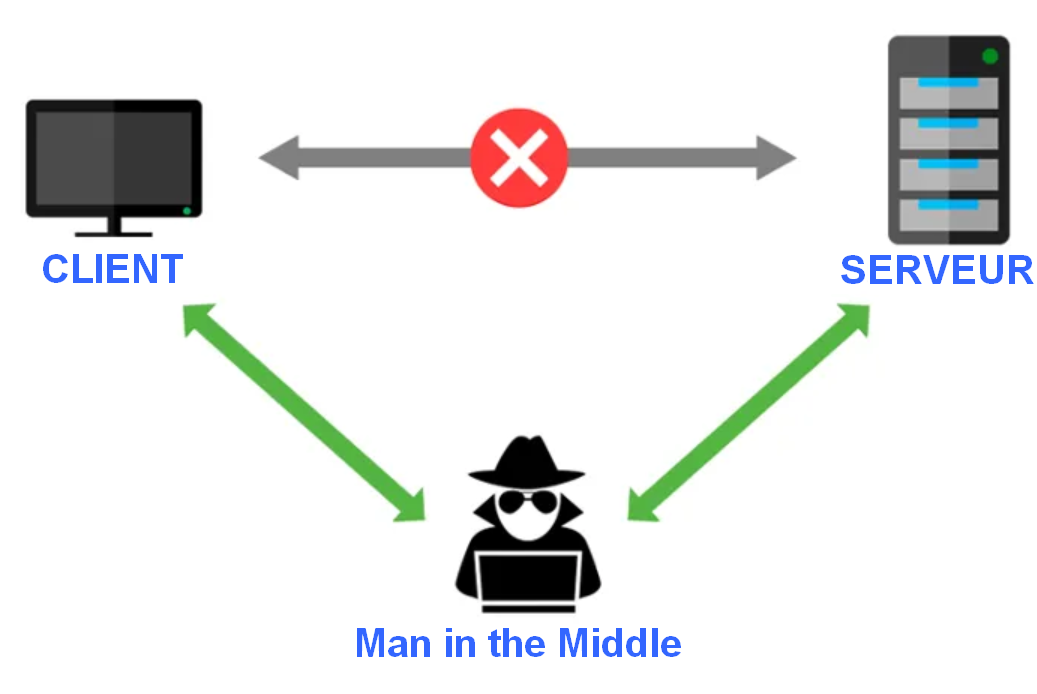
Block-Pi uses Raspberry Pi 4 to setup the external network with its... | Download Scientific Diagram










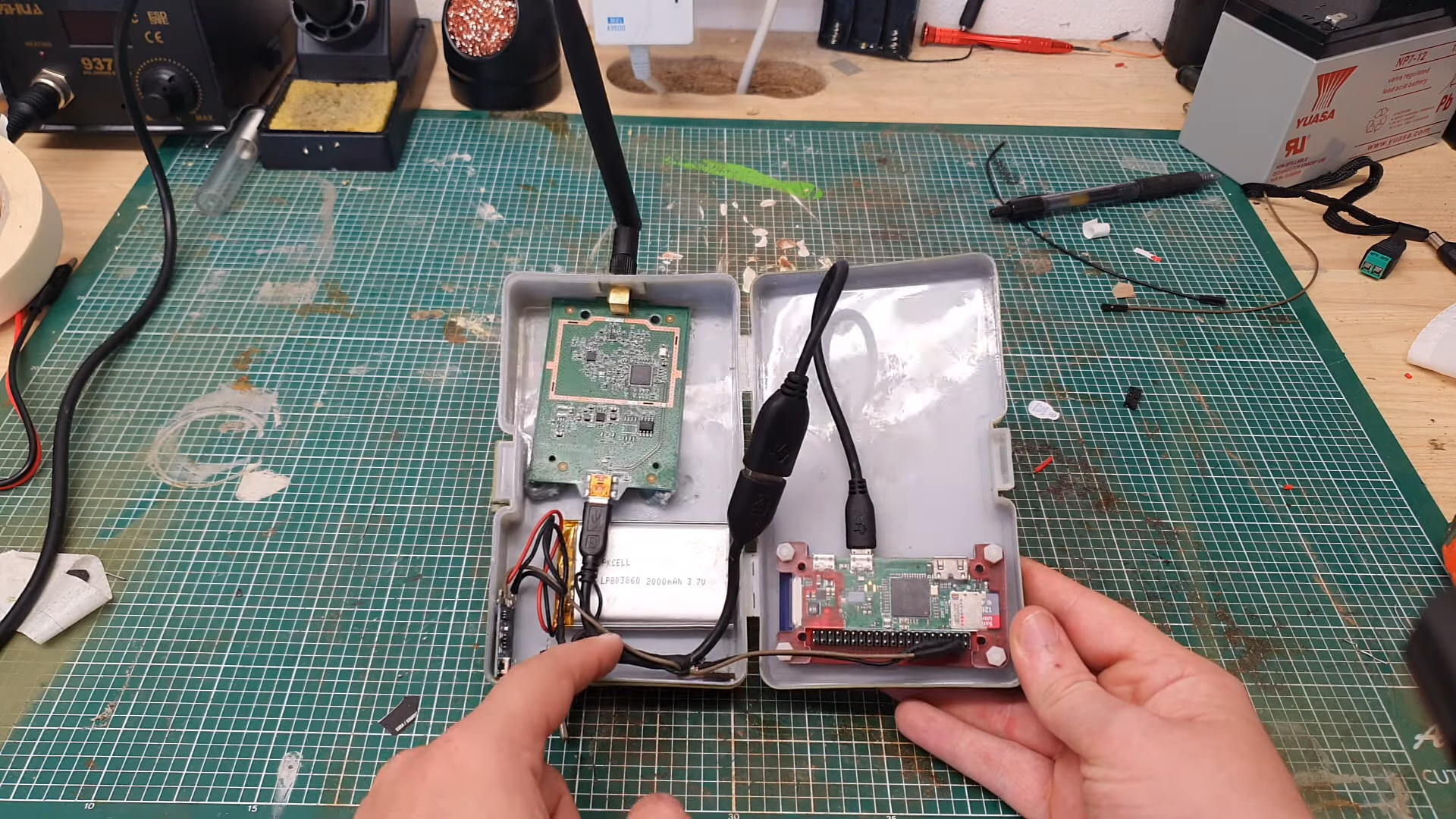



![Build a Pumpkin Pi — A Rogue AP & MitM Framework That Fits in Your Pocket [Tutorial] - YouTube Build a Pumpkin Pi — A Rogue AP & MitM Framework That Fits in Your Pocket [Tutorial] - YouTube](https://i.ytimg.com/vi/tIM-kdmKhnE/mqdefault.jpg)
